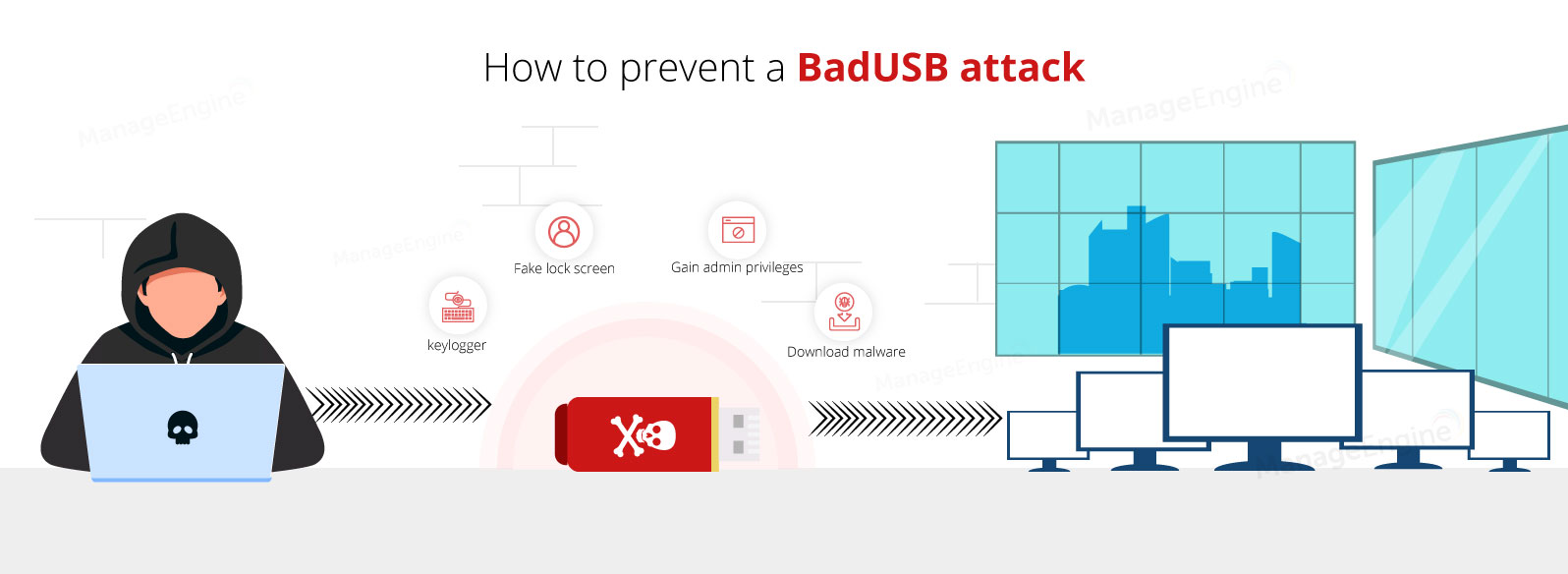
Bow to the USBsamurai: Malicious USB cable leaves air-gapped networks open to attack | The Daily Swig

Yes, Even Your USB Drives Should Be Secured - Directive Blogs | Directive Technology, Inc. | Otsego County, NY

A Click from the Backyard | Analysis of CVE-2020-9332, a Vulnerable USB Redirection Software - SentinelLabs